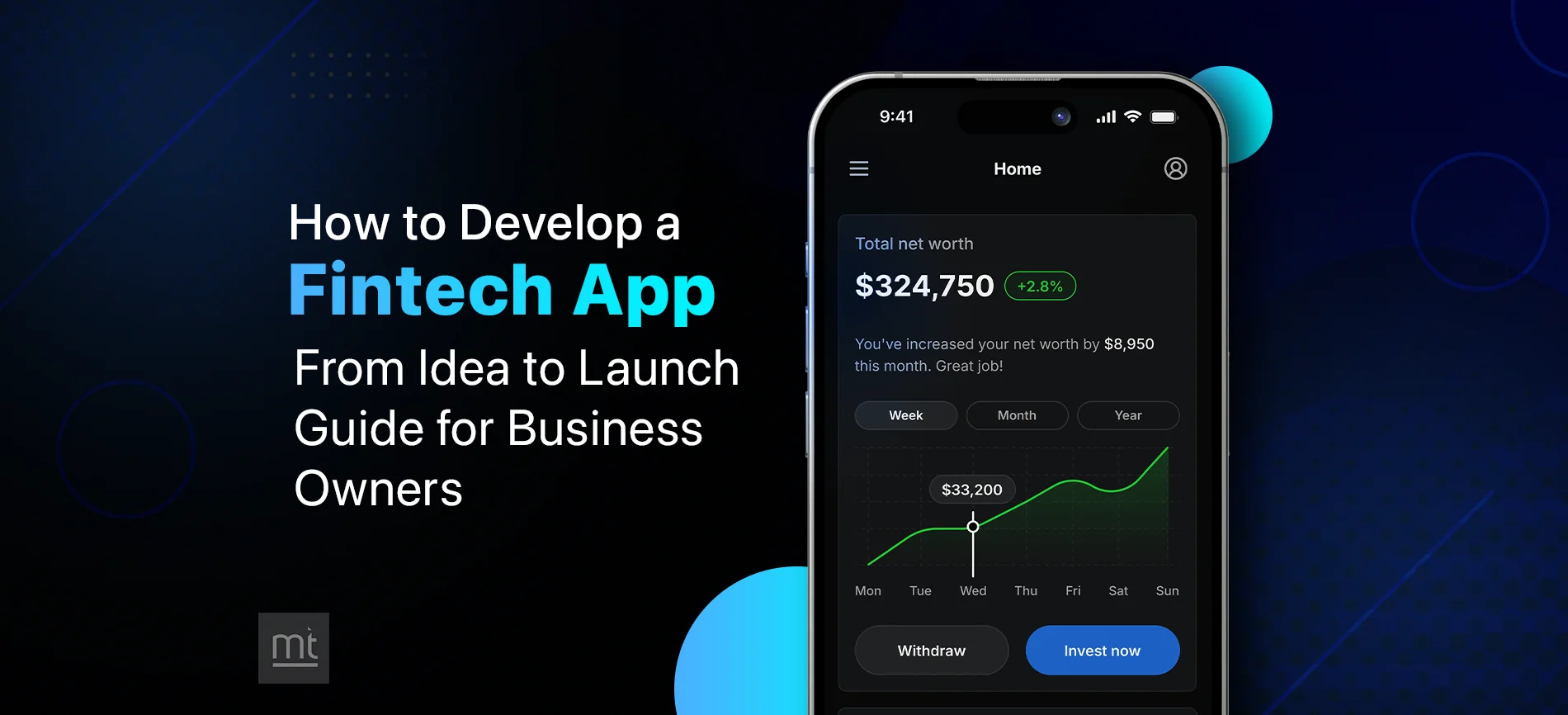
Payment App Development - Cost, Features, Process, And Challenges for Business Owners
 Nikhil Solanki
Nikhil Solanki April 21, 2025

How to Launch an App: A Business Owner’s Playbook for a Successful Mobile App Launch
 Nikhil Solanki
Nikhil Solanki April 04, 2025
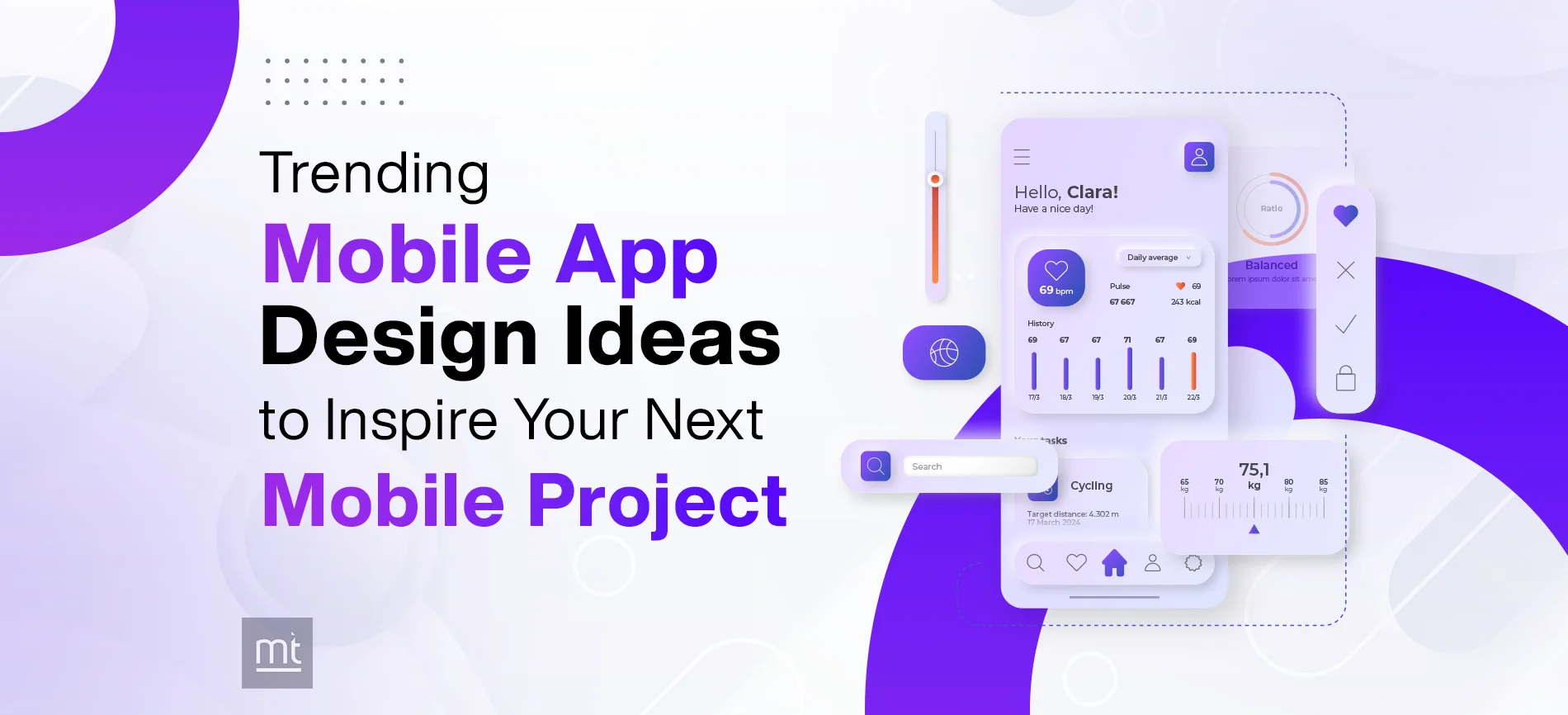
Trending Mobile App UI Design Ideas & Inspiration Examples for Startups to Launch
 Ruchir Pandya
Ruchir Pandya March 07, 2025






![How Much Does It Cost to Develop a Website in 2024? [Checklist]](https://www.manektech.com/storage/blog/image/1700562973.webp)


![How Much Does It Cost to Build a Mobile App? [Checklist]](https://www.manektech.com/storage/blog/image/1708005911.webp)
![Top 10 Software Development Companies in USA [Updated 2025]](https://www.manektech.com/storage/blog/image/1746450897.webp)